Deliverability
Why choose DKIM 2048 over 1024?
Discover why upgrading from 1024-bit DKIM keys to the more robust 2048-bit keys is essential for protecting your emails from fraud and ensuring better deliverability.

PUBLISHED ON
In today's digital world, where trust and security are paramount, ensuring your emails reach intended inboxes is crucial. This is where email authentication protocols such as DKIM (DomainKeys Identified Mail) come in – a vital step in verifying your sender identity and protecting against email spoofing.
However, while still effective, evolving technology and ever-increasing security threats has led to the traditional 1024-bit DKIM key becoming vulnerable. So, what are email senders to do? We'll delve into the reasons why upgrading your DKIM to a stronger 2048-bit key is no longer just an option, but a necessity for safeguarding your email campaign and building trust with your audience.
Table of contents
What is a 1024-bit DKIM key?
What is a 2048-bit DKIM key?
SPF (Sender Policy Framework)
DMARC (Domain-based Message Authentication, Reporting, and Conformance)
Google and Yahoo updates
Table of contents
Understanding DKIM
First of all, what exactly is DKIM? Well, DKIM is an email authentication protocol. It functions like a digital signature by inserting code in the email header, which then gets encrypted.
The recipient's email server checks this code against a public key stored online. If the codes match, it confirms your email is genuine and hasn't been tampered with on the way. This helps prevent scammers from spoofing your email address and increases the chances your email lands in the inbox, not the spam folder.
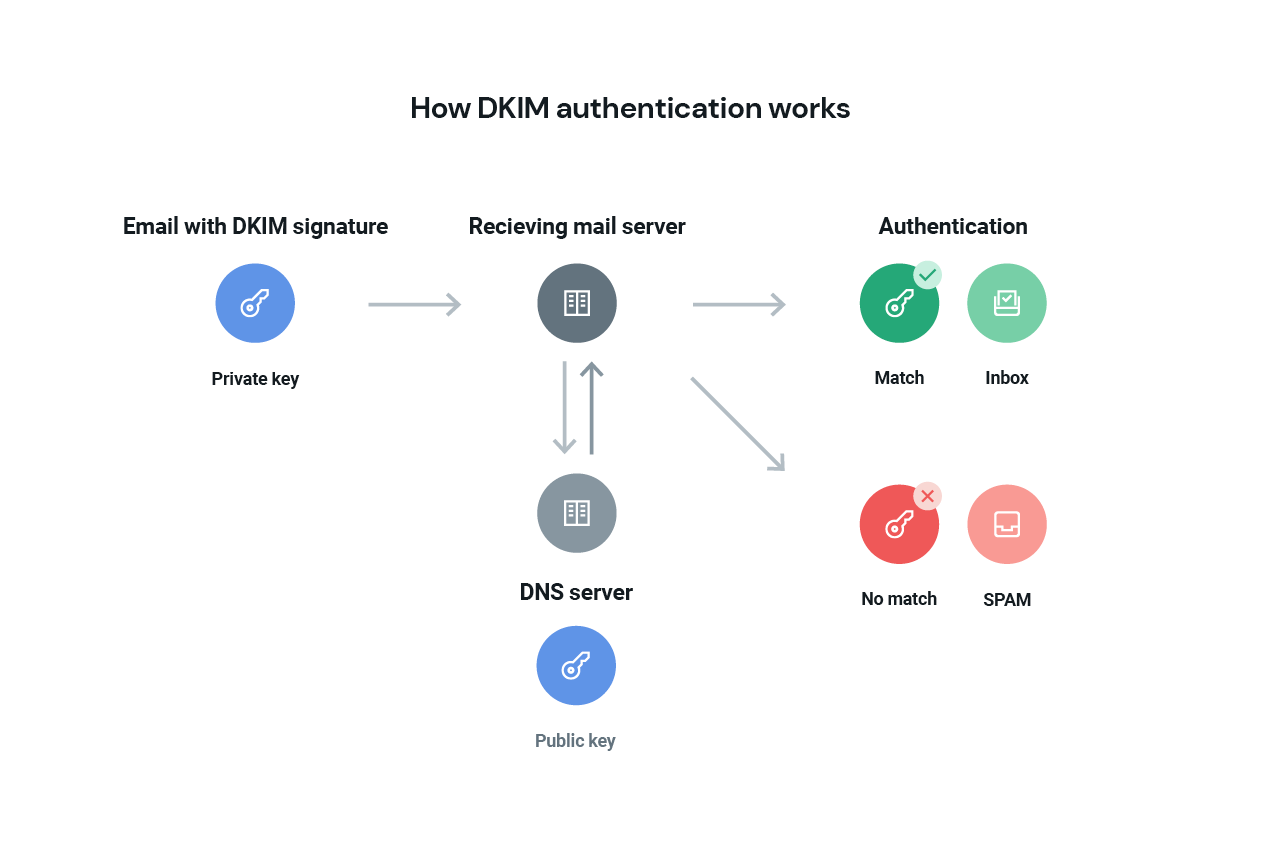
Role encryption keys play in DKIM
In cryptography, key length is crucial as it determines the strength of the encryption. DKIM keys come in various lengths, with 1024-bit and 2048-bit being the most common. The length of the key impacts how difficult it is for an attacker to crack the encryption. Longer keys provide stronger security but may also require more computational resources.
What is a 1024-bit DKIM key?
The 1024-bit DKIM key is the standard cryptographic key used in the DKIM email authentication protocol.
1024 refers to the length of the key in bits; the longer the key and its mathematical complexity, the harder it is for hackers to crack. While 1024-bit keys offered a good level of security in the past, stronger encryption methods are now available.
What is a 2048-bit DKIM key?
One of those stronger encryption methods is the 2048-bit DKIM key. Now, as the name suggests, the primary difference between 1024-bit and 2048-bit keys is the length – 2048 is double that of a standard key.
With double the key length, 2048-bit keys provide significantly stronger encryption and are considered more future-proof. They are the current recommended standard for DKIM.
Email authentication
While most email senders strive to deliver genuine, valuable content to their subscribers, a small number of bad actors spoil the experience for everyone else.
Spammers and phishers constantly try to exploit email systems, tricking recipients into giving away personal information like passwords or infecting their devices with malware. These malicious practices are often disguised as emails from your company, potentially damaging your sender reputation and causing customers to lose trust in your brand. To protect your brand, we strongly recommend you authenticate your campaigns.
Email authentication is a set of techniques used to verify the legitimacy of an email message's origin. It helps to ensure that the email sender is who they claim to be, which is crucial for maintaining the integrity and security of your campaigns.
Now, there are three primary email authentication protocols are:
SPF (Sender Policy Framework)
DKIM (DomainKeys Identified Mail)
DMARC (Domain-based Message Authentication, Reporting, and Conformance).
Each of these protocols serves a unique role in verifying email authenticity and protecting against various types of email fraud. Seeing as we’ve already looked at DKIM, we’ll quickly run through the remaining two protocols.
SPF (Sender Policy Framework)
Imagine you get a letter in the mail, but the return address just says, "Trust me bro Inc." Smells a little fishy, right? The SPF email authentication would be like writing your full company address and authorized mailroom on the envelope.
SPF works by creating a list of exactly who is allowed to send emails from a given domain (like @yourcompany.com). When you receive an email, the recipient's server checks this record to see if the email truly came from an authorized source within the company. This helps prevent scammers from forging email addresses and impersonating your company.
DMARC (Domain-based Message Authentication, Reporting, and Conformance)
Unfortunately, SPF and DKIM are often not enough on their own to ensure your domain’s security. To do that, you’ll need to implement the final authentication protcol – DMARC. This protocol essentially tells receiving servers what to do with messages from your brand when they fail either SPF or DKIM. Here’s how it works:
You set up DMARC like a security setting. It tells email receivers what to do with emails that claim to be from you but fail a check.
When someone sends an email with your address, DMARC checks if the sender is authorized to use it. It's like verifying their ID.
If the email passes, it goes through like normal. But if it fails, DMARC tells the receiver what to do with it, like move it to spam or reject it entirely. This prevents scammers from impersonating you and tricking people.
It’s important to note that both Yahoo and Gmail will require bulk senders to implement DMARC with a minimum policy of p=none which instructs receiving mail servers to log but not to take any action. While on the topic, it�’s worth going through some of the other Yoogle requirements for email senders.
Google and Yahoo updates
Back in February 2024, Google and Yahoo introduced mandatory requirements for email senders aimed at providing a better, more secure inbox experience for users. Now, it’s worth noting that these requirements are simply best practices that have existed for well over 10+ years now. In fact, many email senders already meet them. The difference is they will now be enforced.
Here are three key requirements you will need to prioritize:
Email authentication: Senders will be required to verify their identities with the standard protocols SPF, DKIM, and DMARC.
Add a one-click unsubscribe header: Senders will need to implement a valid List-Unsubscribe header within emails if they haven’t already, to allow recipients to easily opt out.
Only send emails users want: Gmail and Yahoo are getting serious about spam monitoring and senders will need to ensure they’re keeping below a set spam rate threshold.
These mandates will only affect bulk senders. While Yahoo has steered away from giving a definite number, Google has set a figure of 5000 or more messages to Gmail addresses in one day.
We recently sat down with Yahoo’s Senior Director of Product, Marcel Becker, Google’s Director of Product Anti-Abuse and Safety, Anu Yamunan, and Sinch Mailgun’s Vice President of Deliverability, Kate Nowrouzi, to breakdown these new requirements and discuss what they mean for senders. You can watch the full recap below:
Sinch Mailjet now supports 2048-bit encryption
All Sinch Mailjet users’ sending domains will now default to a 2048-bit DKIM authentication, while existing authenticated domains (1024-bit) can be updated to the new standard, providing enhanced security and reliability against sophisticated email threats.
In addition to 2048-bit DKIM, Sinch Mailjet now supports 4096-bit DKIM for even greater security. Again, this allows users to choose a higher level of encryption for their domain authentication needs.








